Imagine PKI as a digital passport system. These passports (digital certificates) are based on a secret-private and a public key duo. They ensure that our digital chats are authentic and private.
Who issues these passports? The Certification Authority (CA). When you’re part of the PKI club, you trust the CA implicitly. Sometimes, there’s a middleman, the SubCA, which gets its authority from the main CA.
In essence, PKI is like the security detail ensuring that our digital world, especially in the realm of EVs, remains safe and trustworthy.
PKI: The Digital Security Maestro
Imagine PKI as a digital security orchestra, harmonizing various instruments like hardware, software, and personnel to produce a symphony of digital certificates. These certificates are like VIP passes, ensuring secure digital conversations.
- Digital Certificates: Think of them as digital ID cards, linking public keys to individuals or systems. They’re issued by a trusted conductor, the Certification Authority (CA). If the signature on the ID is off or it’s expired, it’s no longer valid.
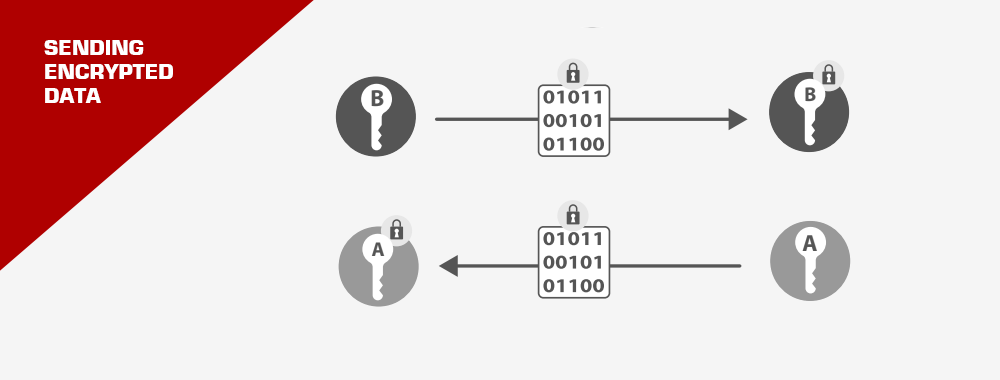
- Keys: These are like secret handshakes. There’s a private one, known only to the certificate owner, and a public one, shared with the world. They’re intertwined in a dance where if one encrypts a message, only the other can decrypt it. This ensures the message’s authenticity and secrecy.
- Security Functions:
- Encryption: It’s like sending a secret letter, where only the intended recipient has the key to unlock and read it.
- Digital Signatures: A seal of authenticity, ensuring the data hasn’t been tampered with.
- Authentication: PKI’s way of saying, “Prove it’s really you!” by verifying the private key.
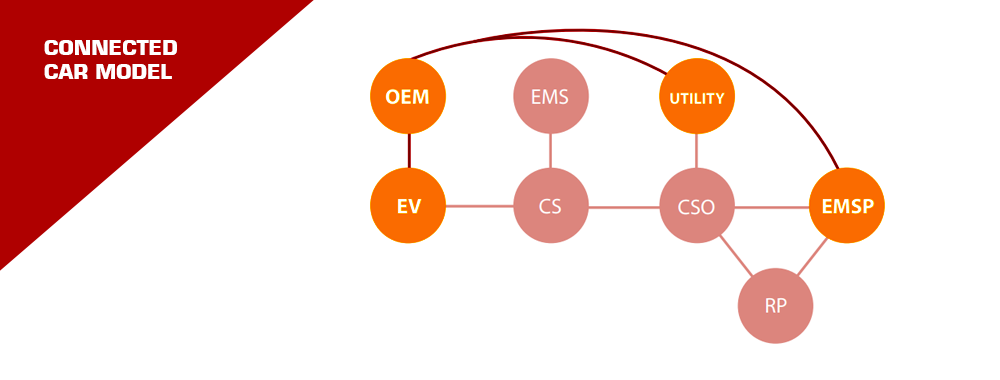
In the PKI ecosystem, every player has the autonomy to craft and manage their certificates, ensuring a robust and flexible security framework.
Trust in the Digital World
For secure digital conversations between organizations, there’s a need for mutual trust. But how do you trust a digital entity? Enter the Certificate Authority (CA). Think of the CA as a trusted mutual friend who vouches for both parties.
Globally recognized CAs, like VeriSign and Digicert, are like the popular kids in school. Their approval (or signature) on certificates is widely accepted and trusted.
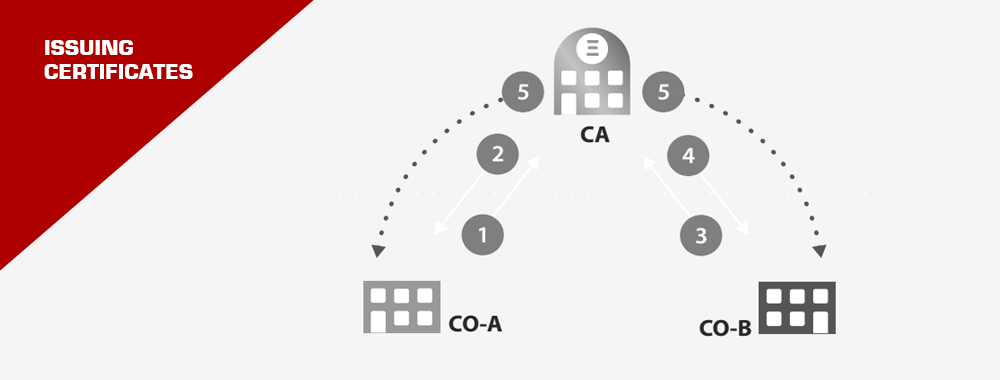
To visualize the process:
- Company A and Company B want to communicate securely.
- They send their public keys to the CA.
- The CA, after verifying, signs these keys.
- Now, both companies can trust and communicate with each other, knowing the CA has vouched for them.
This trust mechanism is embedded in our daily digital activities. For instance, when you securely connect to your bank’s website, it’s the CA’s signature that assures you of the site’s authenticity.
In essence, PKI is the unsung hero, silently orchestrating a secure digital world for us.
The Certificate Hierarchy: A Digital Family Tree
Understanding the Layers
Imagine a family tree. At the base, you have the great-grandparents, followed by grandparents, parents, and finally the children. Similarly, the certificate hierarchy has its own family tree:
- Root Certificate: The great-grandparent of our digital family tree. It’s the certificate of the main Certificate Authority (CA). Think of it as the foundation stone of trust.
- Intermediate Certificate: These are the grandparents and parents. They’re certificates of subordinated CAs, acting as bridges between the root and the end certificates. Why have them? Well, they help categorize certificates, delegate certificate issuance, and most importantly, keep the root certificate super safe (like a treasure locked away).
- Leaf Certificate: The children of our digital family. These are the end certificates, representing individual entities or organizations. Their private keys are special; they don’t sign other certificates.
Why This Hierarchy?
Organizations can wear multiple hats. They can be both certificate users and issuers. For instance, a company might want to issue its own certificates for its various systems and employees. But for these certificates to be trusted outside their ‘family’, they need a stamp of approval from a recognized CA. This is where the SubCA comes in. It’s like a trusted family member vouching for you at a grand event.
The Trust Chain
Imagine a set of Russian dolls. To reach the smallest doll, you need to open each outer doll sequentially. Similarly, to validate a leaf certificate, you need to verify the entire chain above it. This chain of trust ensures that the certificate you’re looking at is genuine and hasn’t been tampered with.
However, like any chain, the longer it gets, the more cumbersome it becomes. More certificates mean more data to verify, which can slow down processes. It’s a balance between trust and efficiency.
Visualizing the Process
A neutral Certificate Authority acts as a trusted middleman, signing certificates of various parties.
This neutral CA can also vouch for certificates via SubCAs. It’s like a grandparent introducing their grandchild through their child. The entire family lineage (or certificate chain) is essential for validation.
In essence, the certificate hierarchy is a beautifully orchestrated system of trust, ensuring our digital interactions are secure and genuine.
The Digital Trust Test: Certificate Validity & Revocation
How to Check if a Certificate is Legit?
Imagine you’re a detective, verifying the authenticity of a precious artifact. Similarly, checking a certificate’s validity involves:
- Date Check: Ensure the certificate is still within its valid date range.
- Trust Verification: Confirm the certificate isn’t a sneaky imposter. This can be done by:
- Storing and comparing with trusted certificates.
- Or, during a digital handshake, exchanging and verifying certificates.
- Revocation Check: Ensure the certificate hasn’t been blacklisted (more on this below).
When Certificates Go Rogue: Revocation
Sometimes, trust is broken. If a Certificate Authority (CA) is compromised, it’s like the key to the city’s treasury being stolen. Every certificate it issued becomes suspect. In the digital realm, this means websites using that CA’s certificate will trigger security alarms.
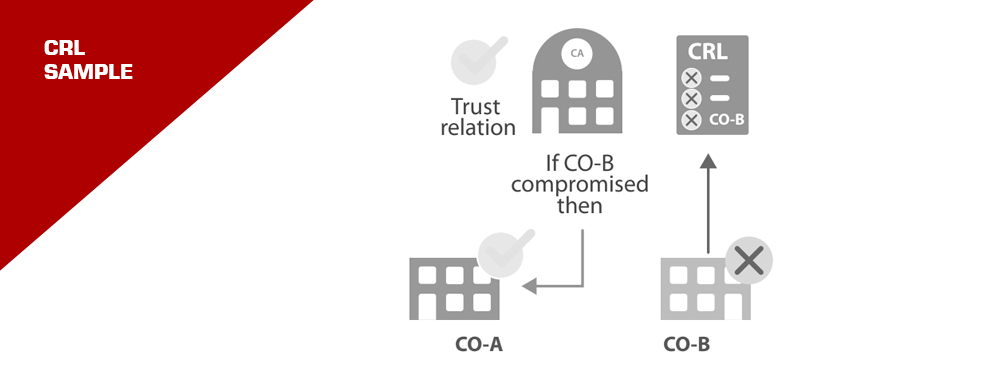
But what if just one organization’s certificate is compromised, say due to a stolen key? That certificate is then “revoked” or blacklisted. It’s like marking a rogue agent in a spy organization.
Visualize this as a tree. If a branch (CA) is compromised, all its leaves (certificates it issued) fall off. But if only a leaf is compromised, just that leaf falls.
The Blacklist: Certificate Revocation Lists (CRLs)
CRLs are like the ‘Most Wanted’ lists for certificates. They’re maintained by CAs and can be accessed online. However, constantly checking these lists can be time-consuming. It’s like a detective constantly checking a long list of suspects.
The Speedy Check: Online Certificate Status Protocol (OCSP)
Instead of manually checking ‘Most Wanted’ lists, imagine having a hotline to the police station for instant checks. That’s OCSP. It’s a dedicated server where you can quickly check a certificate’s status. The response is signed, ensuring it’s genuine.
However, like any system, it’s based on data maintained by the CAs. It’s a faster, centralized way to verify certificates without sifting through multiple lists.
In essence, the world of digital certificates is all about trust. It’s a delicate balance, ensuring our online interactions are both secure and efficient.
Setting Up PKI: The Blueprint
Think of PKI as the foundation of a house. Before you start building, you need a clear plan. For a PKI, this means deciding on the certificates required for secure communication. It’s not just about the tech; it’s about understanding the roles and needs of everyone involved.
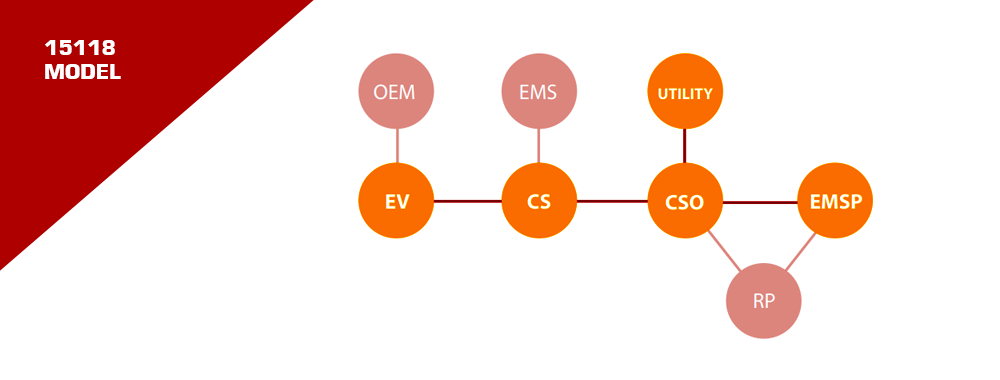
The EV Charging Network: A Web of Players
The EV charging world is bustling! We have:
- EVs: The stars of our show.
- Charging Stations: Where the magic happens.
- Charging Station Operators & E-Mobility Service Providers: The backstage crew ensuring everything runs smoothly.
Every interaction between these players can be secured using certificates. It’s like having secret handshakes between different pairs in a vast network. Everyone has their set of secret handshakes (certificates) to recognize and trust others.
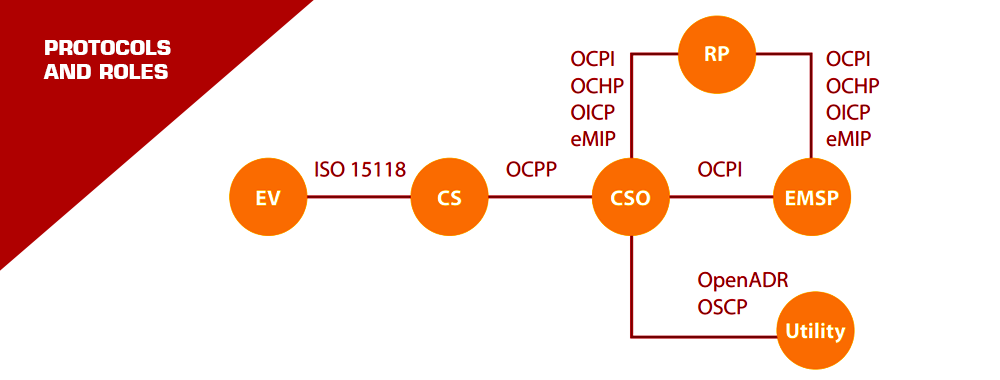
ISO 15118: The Game Changer
When an EV rolls out of the factory, it doesn’t yet know its future E-Mobility Service Provider (EMSP). ISO 15118 comes to the rescue with a mechanism to install the necessary certificates via the Charging Infrastructure. It’s like giving your EV a universal key that can later be tailored to open specific doors.
Complexity & Solutions
PKI, with all its constraints, is like a multi-layered puzzle. ISO 15118 offers techniques to simplify this puzzle. The VDE guide further suggests practical ways to introduce ISO 15118 into the EV market. For instance, having a central store for CSOs to access contract certificates.
Validity Checks: Beyond Just Math
Checking a certificate’s validity isn’t just about crunching numbers. It’s also about verifying the real-world contract behind that certificate. Only an EMSP can do this check, leveraging existing communication channels with CSOs.
In essence, as we zoom into the future of EVs, it’s crucial to have a robust, secure, and efficient system in place. PKI, with the enhancements from ISO 15118, promises to be that guiding light, ensuring our EV journeys are smooth and safe.
ISO 15118: The Gold Standard for EV Charging
Imagine walking into a café, and no matter which coffee brand you prefer, they serve it exactly how you like it. That’s the promise of ISO 15118 for EV charging. It’s all about giving EV drivers a seamless, smart, and secure charging experience, no matter where they are or which service provider they choose.
The Power of Open PKI
PKI, or Public Key Infrastructure, is like the secret handshake of the digital world. It ensures that when your EV talks to a charging station, they’re both speaking the same secure language.
An open PKI design, as detailed in this document, is like opening up this secret handshake to everyone, ensuring:
- Plug and Play: Just plug in your EV, and it knows what to do.
- Open for All: Any market player can join the party.
- Smart Charging: With more data at hand, we can offer better prices, promote green charging, and use our power grids efficiently.
The Road Ahead
The design of the PKI needed for ISO 15118. It’s an invitation for industry leaders and authorities to come together and chart the future.
EV Adept envisions a world where an open PKI for ISO 15118 is the norm, ensuring maximum joy for EV users and propelling the global EV charging market to new heights.
So, as we accelerate into the electric future, let’s champion smart, open standards that benefit us all.
References :
- ChargeUp Europe:
- PKI for EV Charging (Accessed 14 Dec. 2021): Overview of PKI’s significance in EV charging communication and transaction security.
- ElaadNL Testlab:
- Exploring the Public Key Infrastructure for ISO 15118 in the EV Charging Ecosystem: A comprehensive dive into the role and intricacies of PKI within the context of the ISO 15118 standard for EV charging.
- Intertrust Technologies:
- Using PKI to Secure Plug and Charge (Accessed 21 May 2021): Insight into how PKI enhances the security of plug and charge systems.
- arXiv:
- Securing the EV Charging Infrastructure (Accessed 6 May 2021): Exploration of security technology adaptation for EV charging, considering various challenges.
- SAE International:
- SAE PKI Secure EV Charging Project (Accessed 25 Sep. 2020): A project focusing on designing a global EV charging PKI.
- First Test of EV Charging PKI Design (Accessed 27 Apr. 2022): Details on the successful completion of the EV Charging PKI Platform Draft Design.
- OSTI.GOV:
- Cybersecurity for EV Charging Infrastructure (Accessed 1 Jul. 2022): Discussion on public key cryptography, PKI components of ISO 15118-2, and the need for robust cybersecurity in EV charging.
Just installed the Tesla Wall Connector for my Model 3. Absolutely love the convenience! However, I’ve noticed it gets a bit warm. Is that normal or a safety concern? Despite this, the charging speed is impressive. Curious about other’s experiences and any safety tips.
I also use the Tesla Wall Connector, and it does get warm, but shouldn’t be too hot to touch. If it’s excessively hot, you might want to have it checked. Definitely a life-changer for EV owners!
Does anyone have insights on the recent update for the ChargePoint Home Flex? I’ve read about improved efficiency, but I’m worried about losing my presets. Last update was a bit of a hassle. Thoughts?
If you’re driving an EV in cold weather, don’t forget to pre-condition your battery! It’s been a game-changer for my Nissan Leaf, especially in maintaining range. Also, avoid letting your charge drop too low in freezing temps. Any other winter care tips out there?
Great advice! I’d add that using eco mode can help preserve battery life in cold weather. And always keep your charging port clear of ice and snow!
I’m torn between the Chevrolet Bolt and the Hyundai Kona Electric. My top priorities are range and a comfortable interior. Anyone have experiences with these or other suggestions in a similar price range?
Ever since the last update, my Ford Mach-E’s touchscreen has been unresponsive at times. It’s quite frustrating, especially for navigation. Has anyone else had this issue or know a fix?
Trying to decide between the ChargePoint Home Flex and the Blink HQ 100. I like ChargePoint’s app features but Blink’s price point is tempting. Does anyone have experience with both and can offer some insights?
Just a reminder to occasionally check your EV’s battery state of health. I use the JuiceBox 40 and it’s been great for monitoring. Also, avoid rapid charging too frequently to extend battery life. Small habits can lead to a longer-lasting EV. Share your maintenance tips!
Heads up, there’s been a recall for the Volkswagen ID.4 due to a software issue affecting charging. It’s critical to keep up with these updates for safety and performance. Always stay informed and proactive with your EV’s software health!
I’m planning to invest in solar panels to complement my EV charging setup. Considering the SolarEdge inverter for its efficiency. Anyone have experience with this or other solar solutions for EVs? Let’s share insights and possibly bulk buy for better rates!
Cautionary tale: a friend used a non-certified charger and ended up with a fried battery system. It’s crucial to use reputable brands like JuiceBox or Wallbox. Anyone else have safety tips or charger brand recommendations to share?